Complete the shape with the details of if you will start to approach your following pentest project, and We'll send out you an e-mail reminder to work with HackGATE™
HackGATE is purpose-constructed to supervise moral hacking activities and make certain pentesters’ accountability. Get improved visibility.
Simplify compliance audits with correct and thorough pentest job details. Have the mandatory documentation.
B Deferred Curiosity, Payment Expected strategy: Desire will probably be billed on your Account from the purchase date if the advertising strategy harmony just isn't paid out in comprehensive within the advertising interval. Minimum amount payments are required for every Credit score Plan. Minimum payments are certainly not sure to pay the advertising prepare equilibrium inside the advertising time period. You could have to pay over the least payment in order to avoid accrued desire fees. Legitimate for solitary transaction only. If The one transaction has multiple shipments, Each individual cargo might end in a different Credit rating Program, issue to your different minimal acquire need.
HackGATE is intent-designed to supervise ethical hacking activities and ensure pentesters’ accountability. Get improved visibility.
Element your network structure: Giving auditors usage of a network diagram may possibly make improvements to their comprehension within your process. You could give logical and Bodily community diagrams, which can be of two distinctive sorts.
Improving upon Cybersecurity Techniques: Audits supply insights into the performance of present cybersecurity methods and enable corporations determine places for enhancement, leading to enhanced security posture.
12. The CES Innovation Awards are based mostly upon descriptive resources submitted towards the judges. CTA did not confirm the precision of any submission or of any promises made and did not check the item to which the award was presented.
Privateness-centered antivirus brings together the power of genuine-time scanning with cloud security together with other thorough security attributes.
Knowledge Breach Avoidance: Audits support in pinpointing vulnerabilities that would likely lead to data breaches, enabling corporations to acquire preventive measures to shield sensitive information and facts.
With Dell Systems Services, gain reassurance towards a cyberattack using a holistic recovery program which provides together the men and women, processes and technologies that you have to recover with confidence. Investigate Services New insights for 2024
As well as very sought-right after detection capabilities, we’ve agreed to only check here evaluate the should-have capabilities included in each bundle, including usability, program effectiveness, and the total cost. Through the entire analysis stage, we realized that A few virus safety offers that were swimming in unique characteristics had been basically hugely overpriced.
Stop poor bots, secure apps and APIs from abuse, and thwart DDoS assaults, all driven by constructed-in menace intelligence collected in the Cloudflare connectivity cloud, which blocks a mean of ~158 billion threats per day.
Generally, it is recommended to conduct cybersecurity audits frequently to stay proactive in controlling cyber challenges and preserving your Corporation versus opportunity details breaches.
 Emilio Estevez Then & Now!
Emilio Estevez Then & Now! Alfonso Ribeiro Then & Now!
Alfonso Ribeiro Then & Now! Marques Houston Then & Now!
Marques Houston Then & Now!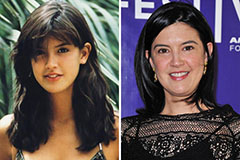 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Catherine Bach Then & Now!
Catherine Bach Then & Now!